Personnel Management
Australian Securty Clearance Tracking
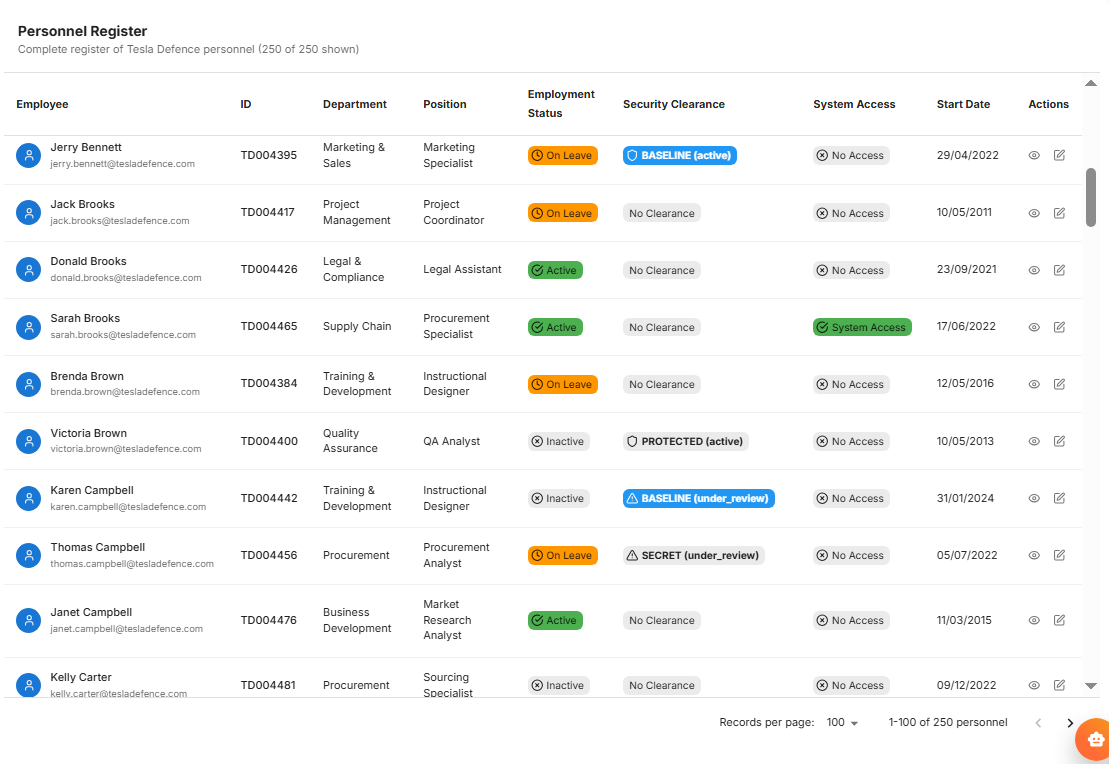
Comprehensive Clearance Coverage
DISPulse provides comprehensive management of Australian security clearances across Negative Vetting Level 2 (NV2), Negative Vetting Level 1 (NV1), and Baseline clearances.
Detailed Record Management and Role-Based Clearance Tracking
Organize, prioritize, and track tasks effortlessly with our intuitive interface.
Automated Renewal Alerts
Automated alerts ensure that renewal processes begin well in advance of expiration dates, preventing lapses that could impact operational capability.

Automated Onboarding Workflows
DISPulse streamlines the personnel onboarding process through intelligent workflows that guide new employees through all necessary security procedures. These workflows automatically adapt based on the individual's role, clearance requirements, and organisational policies, ensuring that all necessary steps are completed in the correct sequence. The system tracks progress through each stage of onboarding, identifies bottlenecks, and escalates delays to appropriate managers. This automation significantly reduces the time required to bring new personnel to full operational status whilst ensuring compliance with all security requirements.
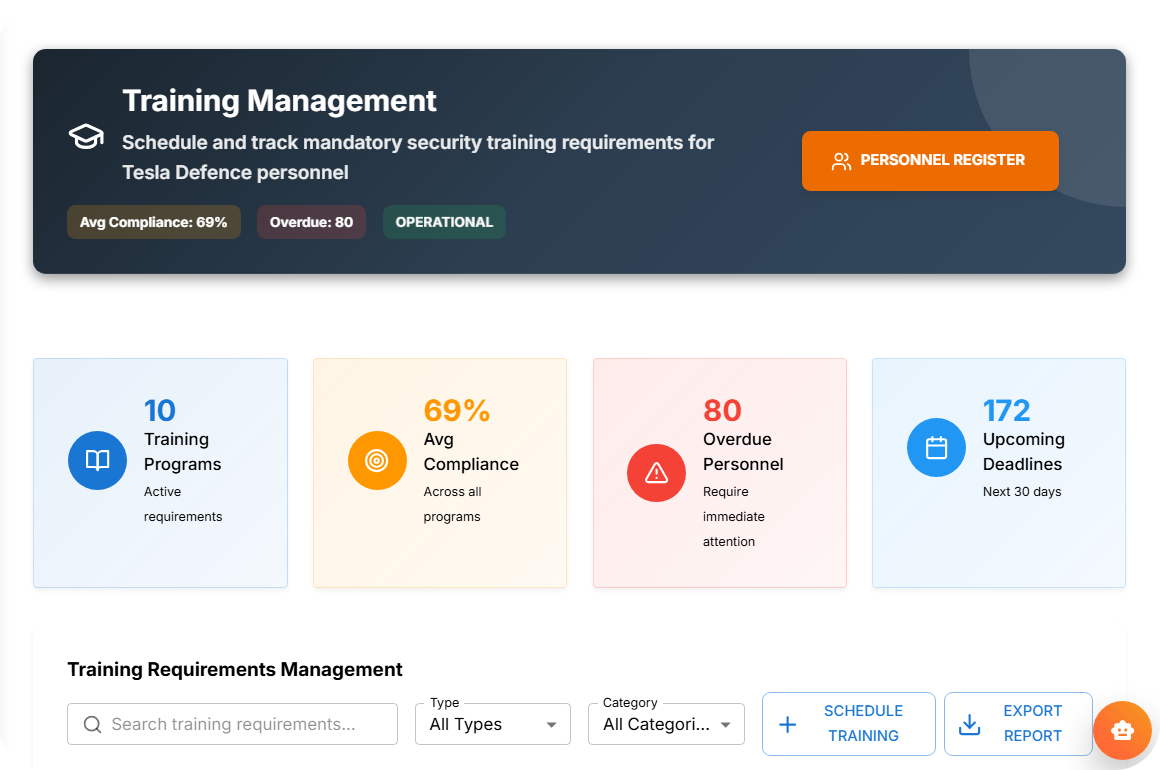
Comprehensive Training Management
The platform's training management capabilities ensure that all personnel maintain current certifications and complete required training programmes on schedule. The system tracks individual training records, identifies upcoming requirements, and automatically enrols personnel in appropriate courses. Integration with learning management systems enables seamless delivery of training content whilst maintaining detailed records of completion and assessment results. The platform also manages training compliance across different roles and clearance levels, ensuring that personnel receive appropriate security awareness and specialised training based on their responsibilities.
Insider Threat Detection
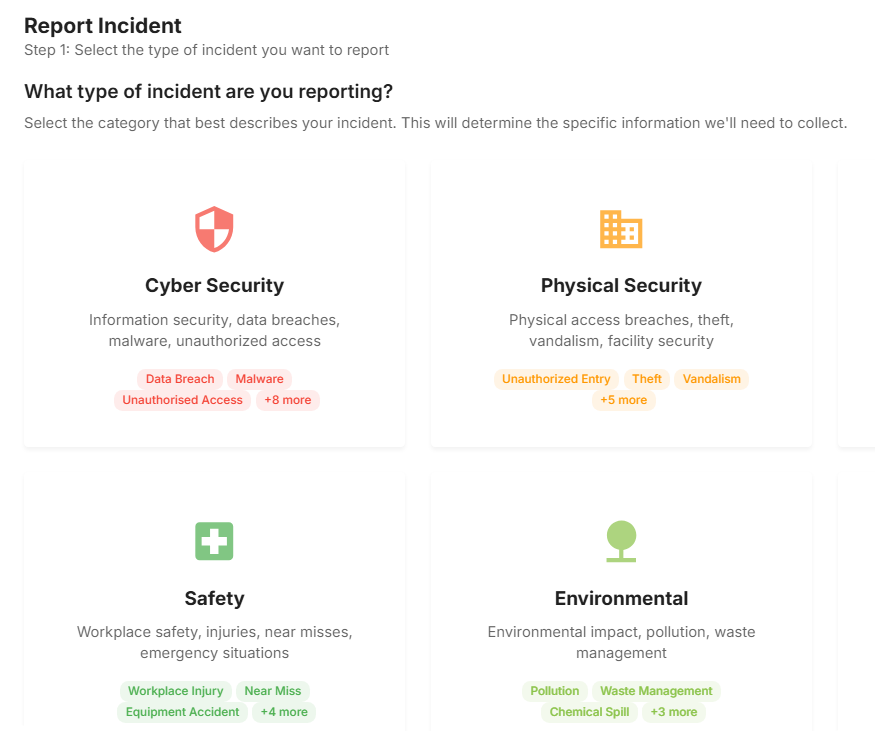
The platform incorporates advanced analytics to identify potential insider threats through pattern analysis and behavioural monitoring. By establishing baseline patterns for individual users and identifying significant deviations, the system can flag potential security concerns for further investigation. This capability extends beyond simple access monitoring to include analysis of work patterns, system usage, and other indicators that might suggest security risks. The system provides graduated response capabilities, from automated alerts to formal investigation workflows, ensuring that potential threats are addressed appropriately whilst protecting individual privacy rights.
